

Why Cybersecurity Is Now a Telco Priority
4 Top Cybersecurity Challenges in the Telecom Industry
3 Core Cybersecurity Strategies for Modern Telcos
Key Tools and Best Practices in Telecom Cybersecurity
Regulatory Compliance and Data Protection for Cybersecurity in Telco Operations
Future Cybersecurity Challenges and Trends in Telecom Cybersecurity
How Telcos Can Operationalise Cybersecurity at Scale
FAQs on Cybersecurity in Telco
Conclusion – Building Trust with Cybersecurity in a Digital-First Telco Era
In early 2024, a major telecom operator in Asia was hit by a cyber attack that exposed millions of user records, including personal details and encrypted payment data (GSMA Mobile Security Framework, 2024). The breach crippled critical services for nearly two days, shook customer confidence, and sparked regulatory scrutiny across the region.
This wasn’t an isolated case. Just months earlier, a leading European telco suffered a massive distributed denial-of-service (DDoS) attack that disrupted mobile and internet connectivity for millions. The attack, traced to a sophisticated botnet targeting its virtualized network infrastructure, highlighted how modern telecom technologies—cloud-native systems, SDN, NFV—can become high-value targets for cybercriminals and state-sponsored actors alike.
So, how can telecom providers protect sensitive data, secure critical telecom infrastructure, and earn trust in an always‑connected, high‑risk digital world? It starts with rethinking cybersecurity as more than just defense — it must be a core part of network design, operations, and innovation. As threats grow more advanced and interconnected, telcos need strategies that not only block attacks but also build resilience, ensure compliance, and strengthen customer confidence at every touchpoint.
Why Cybersecurity Is Now a Telco Priority
Telecom networks carry massive amounts of sensitive data and connect systems across borders, making them high-value targets for cyberattacks. Their global scale and complexity create unique security challenges that few other industries face.
As technologies like 5G, IoT, and cloud continue to expand the attack surface, cybersecurity in telecom has become more than a technical concern. It is now a critical enabler of trust, resilience, and business continuity in a digital-first world.
Why Telecom Networks Are Prime Targets for Cyber Attacks
Telcos do more than connect phone calls or provide internet access. They operate the digital backbone that supports everything from online banking and personal data to government communications and digital wallets. They also manage global signalling systems like SS7, SIP, Diameter, and GTP that allow networks to communicate across borders. Some of these protocols were designed decades ago, long before today’s cybersecurity threats, leaving vulnerabilities that hackers can exploit to intercept calls, read texts, or track locations. With so much sensitive data under their care, telecoms are a prime target for cybercriminals.
Common Threat Vectors in Telecom
Cyberattacks on telcos can take many forms. Beyond weaknesses in network systems, telecom operators face DDoS attacks that disrupt services, SIM-swap fraud that hijacks phone numbers, mobile malware, insider threats, and more. In 2025, AT&T revealed a major data breach that exposed sensitive information from tens of millions of customers. The result? A $177 million settlement and a big hit to customer trust. The breach highlighted how attackers are exploiting both legacy telecom infrastructure and newer technologies like cloud platforms. As telcos continue moving toward virtualised, software-driven networks, strengthening cybersecurity at every layer is essential to protect services and maintain customer confidence.
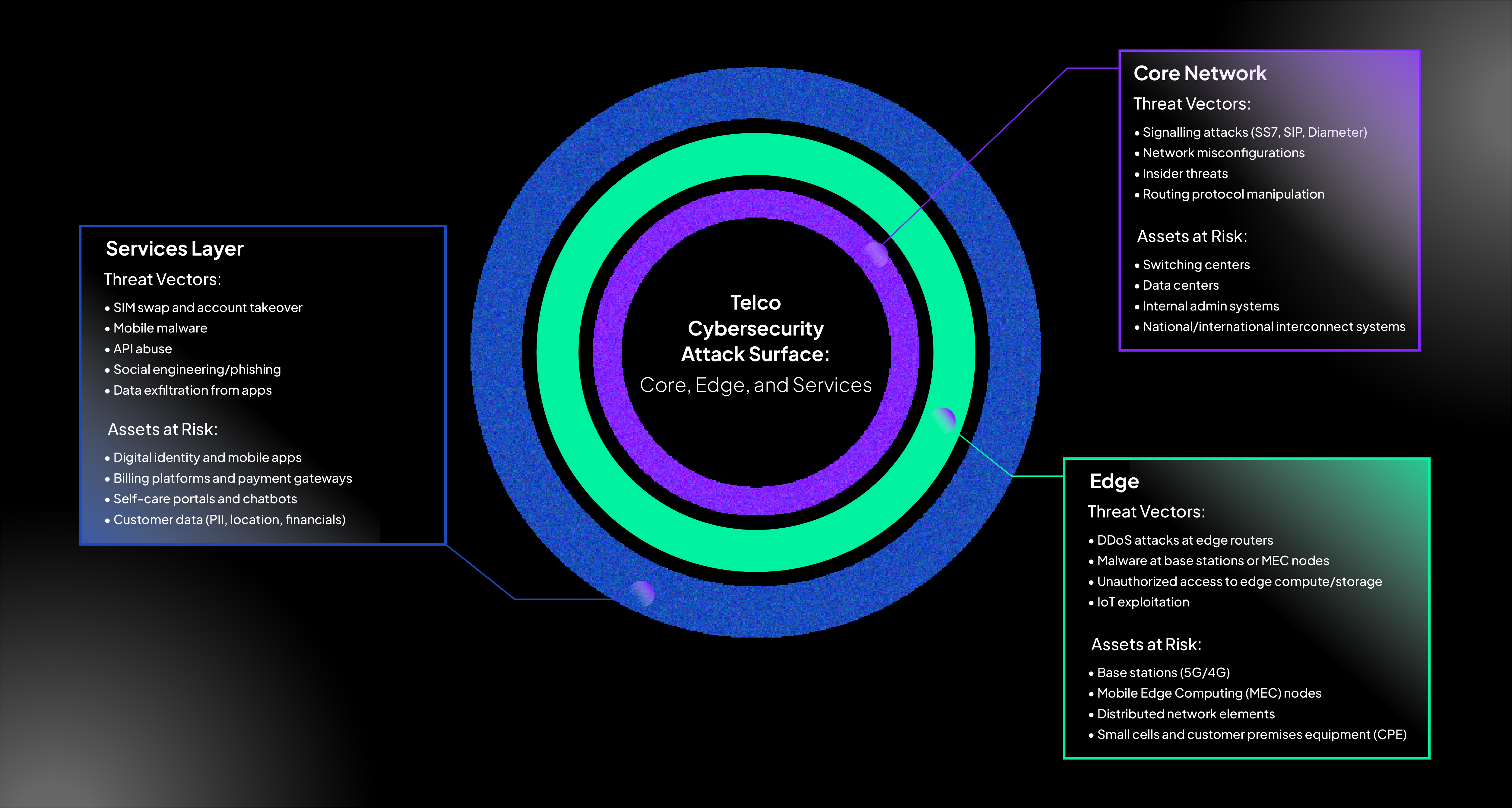
Telco Cybersecurity Attack Surface: Core, Edge, and Services
4 Top Cybersecurity Challenges in the Telecom Industry
As telcos accelerate their digital transformation, they’re also facing a more complex and dynamic threat landscape. From legacy systems to cloud-native infrastructure, here are four key cybersecurity challenges shaping the future of telecom security.
1. 5G Core and Network Slicing Vulnerabilities
5G’s modular architecture offers telcos greater flexibility, but it also introduces new security risks. One of its features - network slicing - lets operators create multiple virtual networks on a single physical infrastructure, each tailored for specific services, from emergency responders to gaming platforms. Every slice introduces its attack surface, and if slices aren’t properly isolated, a compromise in one could become a gateway to the entire network. Imagine an attacker breaching a low-priority slice used for IoT sensors, then pivoting through shared components to disrupt critical communications. The challenge for telcos is to ensure airtight segmentation and monitoring so that flexibility doesn’t come at the cost of security.
2. Risks from Cloud and Virtualisation
Telcos have embraced cloud and virtualized networks to speed up deployments, lower costs, and scale on demand. But these dynamic environments also create dynamic risks. A single misconfigured API, forgotten storage bucket, or excessive privilege can open the door to attackers who can move laterally across systems before anyone notices. Unlike traditional infrastructure, where threats may be more contained, cloud-based breaches can spread quickly. One weak spot in a shared environment has the potential to compromise multiple services. That’s why cloud security must be just as agile, scalable, and precise as the environments it protects.
3. IoT & Edge-Related Threats
Telco networks increasingly connect billions of IoT devices with smart meters, factory sensors, wearable health monitors, and more. Many of these devices ship with weak protections: hardcoded passwords, outdated firmware, or no ability to patch at all. Combine that with edge computing, where data is processed closer to where it’s generated, and you get an environment filled with small, often overlooked entry points. Attackers can target these weaker links to infiltrate networks, disrupt operations, or steal data before it even reaches central systems. For telcos, securing the edge and enforcing IoT standards are no longer optional; they’re essential to safeguarding the entire ecosystem.
4. Legacy Systems and Hybrid Environments
The reality for most telcos is a hybrid world. New 5G cores and cloud-native platforms must coexist with decades-old systems like SS7 signaling or legacy billing software. These older technologies weren’t built with today’s threat landscape in mind, and they often lack modern protections like encryption, authentication, or detailed logging. Attackers know this and look for cracks where old and new connect, exploiting gaps in visibility or inconsistent controls. The challenge isn’t just upgrading technology, it’s managing complexity, securing integration points, and applying consistent policies across a patchwork of systems.
3 Core Cybersecurity Strategies for Modern Telcos
Telecom providers today face cyber threats that are evolving at an unprecedented speed. As networks grow with 5G, cloud-native systems, and edge computing, complexity increases and risks multiply across every layer.
1. Zero Trust Architecture (ZTA)
Traditional perimeter-based defenses are no longer enough. Telcos need security that adapts in real time, stops lateral movement, and responds instantly to sophisticated threats. Zero Trust is built on a simple idea: never trust, always verify. Every user, device, and service must constantly prove who they are, regardless of where they’re connecting from. Telcos bring Zero Trust to life by segmenting networks, enforcing multi-factor authentication (MFA), and applying policies that adjust based on real-time risk signals. A CISA maturity guide shows how this approach helps reduce attack surfaces in complex telecom environments. This dynamic, layered strategy turns security into an enabler for business continuity, regulatory compliance, and innovation.
2. AI-Driven Threat Detection
Attackers now have far more ways to get in. From open APIs to virtualized environments, they are quick to exploit any gap. Traditional rule-based systems can’t keep up with the dynamic nature of cyber threats targeting telecom infrastructure. That’s why telcos are turning to AI and machine learning to monitor vast amounts of network data, identify abnormal behavior, detect botnets, and prevent fraud tactics like SIM swaps. These systems continuously learn from patterns and flag anomalies as they happen, giving telcos the ability to respond before damage is done.
As Mona Nia, Director of AI/ML at Tecnotree, explains:
“With 5G, AI and IoT transforming networks, telecom providers must rethink their cybersecurity posture to counter new-age attacks… Operators must adopt a proactive, AI-driven security strategy to protect networks from evolving threats while ensuring uninterrupted service.”
3. Automation and Orchestration
The more complex telecom networks become, the more important it is to ensure critical services stay protected and uninterrupted. Yet security teams are often stretched thin, unable to waste time on repetitive tasks when threats move at machine speed. This is where SOAR (security orchestration, automation, and response) comes into play. SOAR platforms automate key tasks like patching, alert triage, and threat containment. With built-in playbooks and coordinated workflows, these systems streamline security operations, reduce human error, and speed up incident response. When combined with Zero Trust and AI, SOAR strengthens a telco’s overall defense posture, boosting resilience and agility across the board. In today’s digital-first world, cybersecurity is no longer just an IT function but a strategic priority that protects customer data, sustains operations, and builds long-term brand trust.
Key Tools and Best Practices in Telecom Cybersecurity
Telecom networks face a unique mix of threats from legacy system vulnerabilities to advanced attacks on virtualised infrastructure. That’s why telcos need cybersecurity solutions tailored specifically for their complex, high-value environments. These tools go beyond generic security software, offering layered protection that matches the scale and sensitivity of modern telecom operations.
Signalling Firewalls and Threat Detection
Signalling firewalls and threat detection systems play a vital role in monitoring and blocking suspicious activity across protocols such as SS7, SIP, Diameter, and GTP. These tools help protect the backbone of global communications, as outlined in the ENISA telecommunications security guidelines. As networks expand across borders through cloud and edge deployments, telcos must also navigate data sovereignty requirements, designing infrastructure that balances efficiency, performance, and cost with local compliance obligations.
Network Function Security (VNFs, CNFs)
As telcos shift toward virtualized and cloud-native infrastructures, securing virtual network functions (VNFs) and cloud-native functions (CNFs) through isolation, hardening, and real-time monitoring is crucial to prevent lateral movement and maintain service integrity. This requires weaving regulatory compliance into daily operations, aligning network operations, data management, and customer policies with evolving laws like GDPR, PDPA, and CCPA. Regular reviews, risk assessments, and audits enable telcos to demonstrate accountability to regulators and foster customer confidence.
Identity & SIM Security
SIM swap fraud has become a critical cybersecurity risk in telecom, where compromised credentials can lead to intercepted communications, financial theft, and regulatory consequences. One high-profile 2023 case involved a global SIM swap operation that compromised telco staff and redirected user numbers to intercept two-factor authentication codes—causing financial and reputational damage across the industry.
To combat this, telcos are adopting stronger authentication methods, such as biometric verification, encrypted SIM provisioning, and PKI-backed eSIMs. These technologies help protect subscribers against SIM swap fraud and unauthorised access.
At the same time, telcos have a broader responsibility to uphold consumer data protection. By implementing privacy-by-design, securing the full data lifecycle, and ensuring clear consent management, they strengthen both their defences and customer trust.
Regulatory Compliance and Data Protection for Cybersecurity in Telco Operations
Cybersecurity and compliance go hand in hand for telcos, where success means not just meeting legal requirements, but building resilience and trust at every level. As networks become more global and cloud-driven, telcos must navigate a patchwork of regulations while embedding data protection at the heart of operations.
Regional and Global Frameworks
Telcos operate under an evolving patchwork of regulations, from global frameworks like the GDPR, PDPA, and CCPA, to telecom-specific standards from ENISA, FCC, ITU, and GSMA. These laws govern how personal and operational data is collected, processed, and shared—often across jurisdictions.
Meeting these obligations requires more than checking boxes. Telcos must develop audit-ready systems with proactive governance policies, cross-functional coordination between legal, IT, and operations teams, and automation tools that track regulatory changes in real time.
Leaders in the industry now treat compliance as a business advantage. By embedding practices like data flow mapping, internal policy reviews, and regular risk assessments into day-to-day operations, they reduce exposure while demonstrating transparency and accountability.
Data Sovereignty and Residency
With more data flowing across borders and more services running in the cloud, telcos face increasing pressure to control where data lives. Many countries now require sensitive data such as personal, financial, or government-related information to stay within national borders. That means telcos need infrastructure that complies with local laws but also keeps performance and cost-efficiency in check.
This often involves partnering with local data centers, using region-specific cloud storage, and designing systems that can direct data based on location rules. Telcos also need to stay alert to policy changes, such as shifts in cross-border data transfer rules or updates to residency laws. The key is flexibility. Telcos must build architectures that can adapt quickly without affecting service reliability or user experience. This helps them avoid penalties, reduce legal risk, and maintain seamless operations no matter where they operate.
Telco’s Role in Consumer Data Protection
Today’s customers expect more than privacy policies. They want transparency, control, and accountability. That’s why privacy-by-design is becoming a non-negotiable standard in telco services—from SIM activation to app usage.
This means securing consent clearly, collecting only what’s necessary, and protecting data throughout its lifecycle—using encryption, secure access controls, anonymisation, and timely deletion protocols.
But technology alone isn’t enough. Telcos must also foster a company-wide culture of privacy, training teams on data ethics and reinforcing internal accountability.
Done right, strong data protection does more than prevent breaches. It builds customer trust, enhances brand reputation, and ensures long-term success in a market where data integrity is directly tied to business performance.
Future Cybersecurity Challenges and Trends in Telecom Cybersecurity
As digital networks evolve, telcos face a future filled with both risks and opportunities. Emerging technologies promise faster speeds, smarter services, and stronger connections, but they also introduce security challenges that could reshape the telecom landscape.
Quantum Threats and Post-Quantum Cryptography
Quantum computing could break today’s encryption faster than many expect, putting sensitive data, communications, and transactions at risk. A global poll by ISACA found that 62% of cybersecurity professionals believe quantum will defeat current cryptography before systems are ready, yet 95% of organizations lack a quantum-safe plan. The threat isn’t theoretical. Bad actors could use “harvest now, decrypt later” strategies to steal and store encrypted data today, to crack it once quantum tools mature. Public awareness, however, remains limited. A UK survey showed 60% had heard of quantum computing, but only 11% felt they understood it well. Telcos must act early, investing in post-quantum cryptography standards and working with industry bodies to future-proof critical systems before attackers gain the upper hand.
Cybersecurity-as-a-Service (CaaS)
As cyber risks rise, telcos aren’t just defending their networks; they’re evolving into security providers. CaaS allows operators to offer managed security services to enterprises, small businesses, and even consumers, turning defense capabilities into a revenue stream. Deloitte’s 2022 Telecom Industry Outlook highlights how telcos are embedding cybersecurity into their value propositions in the 5G and soon 6G eras, offering services like threat monitoring, incident response, and endpoint protection. But while these offerings have promise, trust remains an obstacle. A Cisco Consumer Privacy Survey found that only 38% of consumers feel confident that their telco can protect personal data. For telcos, CaaS isn’t just about business opportunity — it’s a chance to reshape customer trust and loyalty by delivering visible, effective protection.
6G Security Considerations
6G promises a revolution in connectivity ultra-low latency, AI-native network operations, and trillions of connected devices forming intelligent ecosystems. But these advances will introduce unprecedented attack surfaces, from AI model manipulation to large-scale IoT vulnerabilities. Security must be designed into 6G architecture from the ground up, with standards addressing privacy, integrity, availability, and resilience. This means telcos, regulators, and technology partners will need to collaborate early to set security benchmarks for 6G that can keep pace with innovation. The operators that succeed will be those that see security not as an afterthought, but as a defining pillar of 6G’s value and success.
How Telcos Can Operationalise Cybersecurity at Scale
Putting a strong cybersecurity plan into action takes more than good tools or policies. It demands thoughtful design, targeted investment, and a security culture that’s woven into every part of the organization.
Security-by-Design Principles
Modern telcos can no longer afford to bolt on security at the end of development cycles. Security-by-design means embedding protection at every stage, from architecture and code to operations and customer experience. This includes adopting DevSecOps practices, integrating automated security checks into CI/CD pipelines, and using real-time monitoring and threat detection to catch risks before they escalate. By prioritizing privacy-by-design and secure API development, telcos can build networks that are resilient by default to protect both their infrastructure and customer data as they scale.
Security Talent and Organizational Culture
Technology alone doesn’t stop cyber threats, people and culture make the difference. Telcos need skilled cybersecurity professionals who understand both telecom-specific risks and evolving threat landscapes. This means investing in upskilling internal teams, building cross-functional collaboration between security, IT, and network operations, and fostering a culture where every employee sees themselves as part of the defense. Regular training, realistic phishing simulations, and clear communication channels for reporting risks all help build a security-first mindset that extends across the organization.
Budget Allocation and ROI Tracking
Cybersecurity is no longer just a cost center — it’s a critical investment in business continuity, customer trust, and regulatory compliance. Leading telcos allocate budgets strategically, focusing on areas with the highest impact: proactive threat prevention, faster incident response, regulatory readiness, and innovations that protect both data and network performance. Just as important is tracking ROI: operators must measure outcomes through metrics such as breach detection times, response speed, compliance audit results, and customer trust indicators to ensure that cybersecurity spending truly delivers business value.
Case Study: How Optus Recovered After the 2022 Breach (Australia)
In September 2022, Australia’s second-largest telco, Optus, suffered a major data breach that exposed personal details of around 10 million customers, sparking public outrage and regulatory action. Optus responded fast by setting up a crisis team, funding passport replacements, providing credit monitoring, and overhauling API security and incident response processes.
The case proves that with the right design, culture, and investment, telcos can successfully implement strong cybersecurity measures and rebuild trust after even the most serious breaches.
FAQs on Cybersecurity in Telco
What is Zero Trust, and why is it relevant for telcos?
Zero Trust means no user, device, or system is trusted by default — everything must be verified. This approach is crucial for telcos managing millions of connections across complex networks. By enforcing strict access controls and continuous checks, Zero Trust helps stop attackers from moving laterally if they breach the outer defenses.
How does 5G increase cybersecurity risks?
5G expands the attack surface with open APIs, multi-tenancy, and decentralized architectures. These features create more entry points for attackers and make monitoring harder. That’s why telcos are adopting AI-driven detection, automation, and Zero Trust models to secure 5G from the ground up.
What’s the difference between telco security and IT security?
Telco security covers unique challenges beyond standard IT, like protecting signalling protocols (SS7, SIP, Diameter) and managing network slicing in 5G. These systems handle huge volumes of sensitive traffic and need protections tailored to large, distributed networks.
How are telcos preparing for post-quantum encryption?
Telcos are testing quantum-resistant algorithms and joining global efforts to develop standards for post-quantum cryptography. The goal is to future-proof communications against the risks quantum computing may bring.
Conclusion – Building Trust with Cybersecurity in a Digital-First Telco Era
Cybersecurity in telecom is more than a technical safeguard — it’s the foundation of trust, innovation, and resilience for modern telcos. In today’s hyper-connected world, telecom operators aren’t just delivering connectivity but also safeguarding the digital experiences that people and businesses rely on every day. As operators roll out 5G, cloud, IoT, and edge computing, securing networks, data, and digital interactions becomes central to earning customer confidence, meeting regulatory demands, and driving sustainable growth.
From managing SIM cards to adopting eSIMs, supporting digital wallets, and enabling online payments, telcos have a critical duty to embed security into every layer of their operations. This commitment to protection enables innovation, fuels digital transformation, and positions telcos as trusted partners in a rapidly evolving landscape
In a digital-first world, resilience isn’t optional, it’s essential. That’s why circles.co is built to keep you connected, secure, and ahead of the curve.
